In the previous three chapters, we introduced all 35 visible optical anti-counterfeiting technologies developed by Image Technology.
These overt security features can be identified directly with the naked eye, enabling fast and intuitive authenticity verification by consumers and inspectors. The series has garnered strong interest and received positive feedback from readers across various industries.
However, as counterfeiting techniques continue to evolve, visible security features alone are no longer sufficient. To address increasingly complex security challenges, Image Technology (IMAGE TECH) continues to advance optical innovation and expand into higher-level, covert security solutions.
Introduction to Covert Optical Anti-counterfeiting Technologies
In this chapter, we begin introducing Image Tech’s covert optical anti-counterfeiting technologies.

Unlike overt features, covert security elements cannot be recognized by the naked eye. They require specific tools, lighting conditions, or optical principles to verify, offering stronger concealment and significantly higher security levels.
This article focuses on the first eight covert optical security technologies, including:
- Micro Text
- Multi-channel Micro Text
- Laser-readable features
- Light field imaging
- Multiple image writing technologies
Covert Optical Security Technologies (I)
1. Micro Text
Micro text is a security technique that reduces text or graphics to a precise scale before printing.
The reduced content cannot be read with the naked eye and requires a 40×–200× magnifier for verification.
The security strength of micro text lies in precise control of scaling ratios and printing resolution.
By adjusting these parameters, highly counterfeit-resistant security elements can be created.
At Image Technology, micro text precision is strictly controlled, with a minimum character height of 30 microns, while maintaining clear readability after reduction.
2. Multi-channel Micro Text
This technology presents 2–4 different micro text images at the same position under a microscope when illuminated from different directions.
Each lighting angle reveals a different micro image, significantly increasing verification complexity and anti-copy capability.
3. Covered Laser Readable
Covered laser-readable technology reveals predefined static or dynamic images or text when a laser pointer illuminates a concealed area at a specific angle.
This feature is based on laser holography and optical diffraction principles, making it extremely difficult to replicate without specialized equipment.
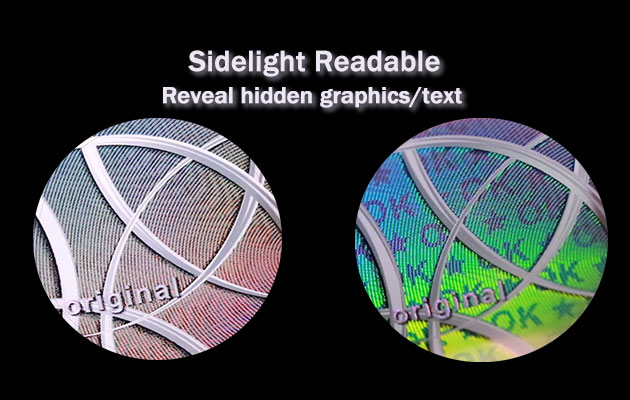
4. Sidelight Readable
Hidden images or text become visible when light enters the substrate at an angle of approximately 15° from the edge. Under normal viewing conditions, the feature remains invisible, ensuring strong concealment.
5. Point Light Readable
Also known as mobile-phone verification, this technology reveals hidden information under illumination from a small point light source.
Strict requirements for illumination angle and distance ensure that the security feature remains undetectable during everyday use.
6. Light Field Image
Under point-light illumination, this feature produces deep spatial diffraction images with strong visual depth. Even when partially covered, contaminated, or damaged, the complete image can still be reconstructed, ensuring reliable authentication.
7. Multiple Image Repeated Writing
Also known as holographic data storage, this technology records multiple images or texts in the same area. Using dedicated equipment, different images can be retrieved at different viewing angles, providing advanced multi-level security.
8. DOE-Generated Diffraction Pattern
When illuminated by a laser or a point light source, symmetric or asymmetric images appear around the zero-order diffraction region. This feature offers high resistance to scanning, copying, and digital reproduction.
Looking Ahead
The eight technologies introduced in this article represent the first group of Image Technology’s covert optical anti-counterfeiting solutions.
Driven by continuous innovation, we are expanding our optical security portfolio to prevent counterfeiting before it happens.
In Part 5, we will introduce the remaining seven covert optical security technologies, including:
- Digital graphic encryption
- Fiber encryption
- Micro-code technologies
Stay tuned for the next chapter of the Optical Anti-Counterfeiting Technology Series.






